
Ukrainian Hackers Allegedly Cut Off Russian Soldiers' Beloved Vodka Supply

Tech blog Bleeping Computer spotted reports yesterday that multiple distributed denial of service — a type of attack that overwhelm a server by flooding it with junk traffic — had disrupted alcohol sellers' access to a portal used by the Russian government to coordinate distribution of ...
Security researchers: Here's how the Lazarus hackers start their attacks | ZDNet

Liam Tung is a full-time freelance technology journalist who writes for several Australian publications.
The Lazarus hacking group is one of the top cybersecurity threats from North Korea, recently catching the attention of the US government for massive cryptocurrency heists.
Hackers are using trusted company names in scams
/cloudfront-us-east-1.images.arcpublishing.com/gray/6W4AM2PTTFDD7KN54ZI4QVKC2U.bmp)
"Not realizing it didn't have a Norton's logo or letterhead. I acted out of 'Hmm how dare they.' because it was more than I had paid the last year," she said.
"This guy's name was Steve and he sounded like he could have been my grandson - calling from Dallas. 'We are looking out for you Ms. Estelle. We are looking out for you, but please don't notify anybody.'"
Hackers threaten Supreme Court over Roe - Must Read Alaska

Hackers Using PrivateLoader PPI Service to Distribute New NetDooka Malware
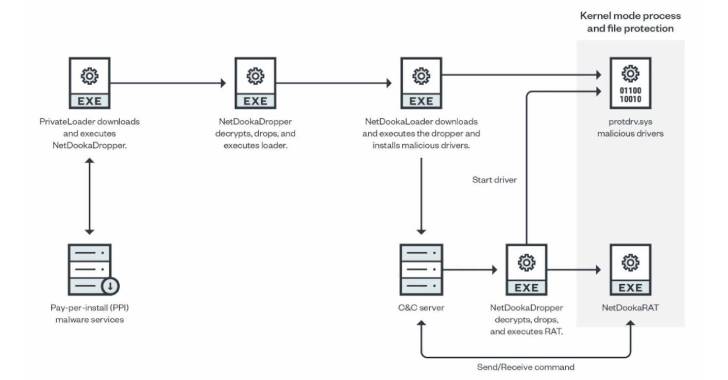
A pay-per-install (PPI) malware service known as PrivateLoader has been spotted distributing a "fairly sophisticated" framework called NetDooka, granting attackers complete control over the infected devices.
"The framework is distributed via a pay-per-install (PPI) service and contains multiple parts, including a loader, a dropper, a protection driver, and a full-featured remote access trojan (RAT) that implements its own network communication protocol," Trend Micro said in a report published ...
Just Sayin': Hackers will try anything to get your money | Mineral County WV News and Tribune | ...

"Hello, can you help me? I got a new phone and can't log into my Facebook. Can you help me get a code so I can log on?"
Nothing about those words seems very alarming, especially since the request came to you from a friend. Yet in this day and age it is really hard to tell friend from foe, because who you think is your friend may turn out to be a hacker trying to gain access to your Facebook account.
US Sanctions Cryptocurrency 'Mixing' Service for Aiding North Korean Hackers | PCMag

The sanctions target Blender.io, a website that charges to “anonymize bitcoin transactions” by mixing it with funds from other users.
In addition, the US Treasury Department is signaling it’ll go after other cryptocurrency mixing services that are found helping hackers. The sanctions against Blender.io essentially outlaw US persons and groups from conducting any business with the cryptocurrency service.
Bug Bounty Programs Help EU Firms Beat Hackers | PYMNTS.com

Cyberthreats have heightened in the wake of the pandemic and fraudsters getting more sophisticated by the day, creating countless threats and vulnerabilities that require businesses to stay on top of their game to safeguard their data and systems from attackers.
"They come to us and tell us, 'You can test us, we're not afraid,'" De Ceukelaire told PYMNTS in an interview, adding that it doesn't take long for that confidence to drop. "In more than 70% of all cases, a high to critical vulnerability is detected within 48 hours."
Researchers uncover a new #cyberespionage campaign by Chinese "Mustang Panda" hackers using PlugX implant, custom s… https://t.co/i2gI4lVkGZ TheHackersNews (from The Internet) Fri May 06 07:22:38 +0000 2022
Chinese government-linked hackers have tried to steal sensitive data from some three dozen manufacturing and techno… https://t.co/bJls6IU6Xx CNN Wed May 04 09:08:29 +0000 2022
China's Winnti hackers (also tracked as APT41, Blackfly, and BARIUM) have been spotted stealing sensitive proprieta… https://t.co/wmu5vZIBpB TheHackersNews (from The Internet) Wed May 04 13:11:07 +0000 2022



No comments:
Post a Comment