
Cyber Command assessed that the malware , which it posted to the information sharing platform VirusTotal , is being used in ongoing cyberattacks aimed at the financial sector.
"These malware samples are currently used for fund generation and malicious cyber activities including remote access, beaconing, and malware command by malicious cyber actors," the command said in a tweet.
The alert comes just weeks after a meeting with North to discuss possible denuclearization with the U.S. in Stockholm failed to produce a deal, just the latest in a series of meetings where both the U.S. and North Korea have walked away without a resolution.
Check out this next:
Hackers mount 'large-scale' cyber attack on Labour Party systems | BT
Hackers have mounted a “sophisticated and large-scale cyber attack” on Labour’s digital platforms, the party has said.
A spokeswoman said the incident had been reported to the National Cyber Security Centre but they were confident that no data breach had occurred.
Some campaigning activities were temporarily slowed, but the systems were back up to speed by Tuesday morning.
“We took swift action and these attempts failed due to our robust security systems. The integrity of all our platforms was maintained and we are confident that no data breach occurred.
Hackers Claim 'Any' Smartphone Fingerprint Lock Can Be Broken In 20 Minutes

Owners of almost every Android smartphone, and iPhones up to and including the iPhone 8, could have a new security problem to worry about: Chinese hackers claim to be able to beat any fingerprint scanner in just 20 minutes.
Unless you have invested in a smartphone such as the iPhone 11 that has done away with fingerprints as a biometric security measure, the chances are you rely upon that finger image to unlock your device and many of the apps within. Which could be bad news as Chinese hackers have demonstrated how, they say, any fingerprint scanner can be beaten using equipment costing $140 (£108) and an app that analyzes a photograph of your print.
Israeli cybersecurity startup's plan to keep trains safe from hackers

Railroads are operating on ancient technology platforms that were created long before today's cyberthreats, says Amir Levintal, CEO of rail-focused cybersecurity start-up Cylus .
The problem affects only a small niche of industry, but it nonetheless worries many experts and lawmakers.
More from Upstart 100:
Amazon has triggered an arms race in this technology
How Beddr and other tech start-ups could help millions of Americans get a good night's sleep
This start-up aims to break internet monopolies and deliver 5G broadband for $49 a month
Check out this next:
Hackers can trick your Android to gain access | Komando.com

Where there's an internet connection, there are clever hackers looking to exploit users. This isn't just limited to computers — all our connected devices are at risk.
Hackers can access the phone's direct connection to its carrier — opening the doors for stronger spying and service shutdowns. If you use an Android phone, here's what you need to know about this scary new security vulnerability.
According to an exclusive report from TechCrunch , security researchers at Purdue University and the University of Iowa have discovered a security flaw that can allow hackers to access one of the deepest parts of an Android phone: the baseband. This system is how a phone makes a connection to its carrier and is responsible for the voice and data networking of any smartphone.
How To Protect Yourself From Hackers While Holiday Shopping Online | wfmynews2.com
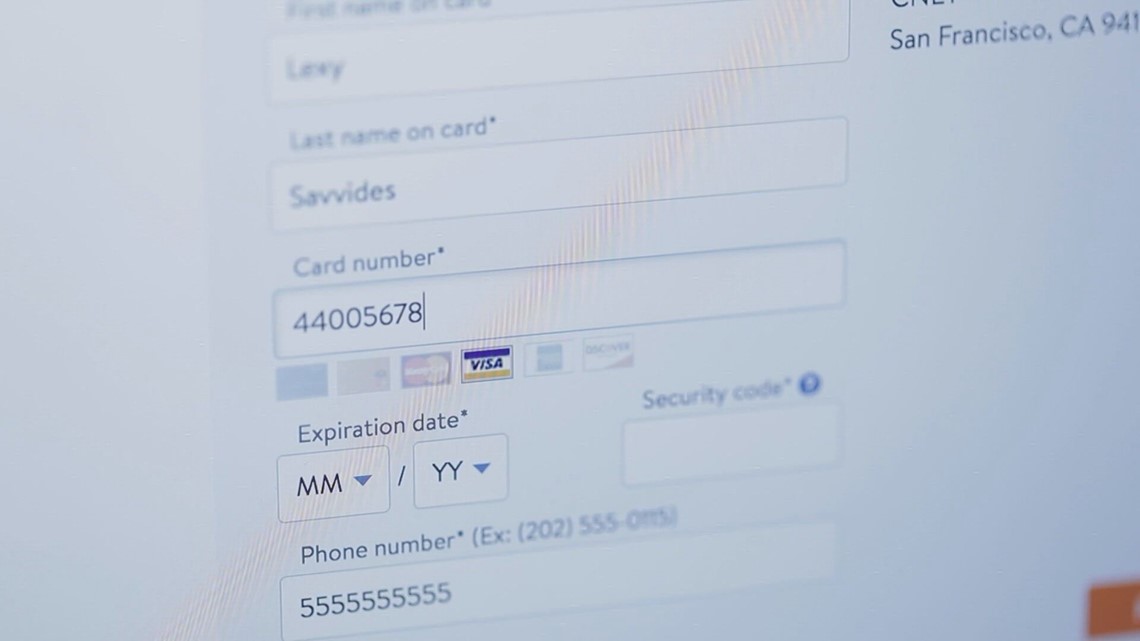
GREENSBORO, N.C. — As you're holiday shopping, you might consider skipping the stress of heading to a physical store and shop online instead.
Credit monitoring company Experian says 43% of holiday shopping identity theft happens online.
* * *
"If you are on the retailer's website and it just kind of looks like it was built in 1985, maybe there is no contact information, maybe there is no physical address, no phone number, those are all red flags that the website may not be legitimate," he said.
Hackers Dissect 'Mr. Robot' Season 4 Episode 6: 'Not Acceptable' - VICE
Micah: The episode was called Not Acceptable, and the theme was pretty clearly people doing unacceptable things.
* * *
Micah: We don't know what he did to her yet. She called Elliot and convinced him to meet her, but it was a trap. Maybe she's just hoping this will let her get away unscathed.
Emma: Oh, for sure. Even without coercion... I just tweeted about this . The records being there mean they can be compromised.
Suspected hacker's extradition focuses attention on Israeli-American in Russian jail

MOSCOW — An Israeli Supreme Court decision to extradite an alleged Russian hacker to the U.S. has thrown into question the fate of an Israeli-American woman in Russian custody.
* * *
Naama Issachar, a dual U.S.-Israeli national, got what many believe to be a sentencing wildly disproportionate to the crime: seven and a half years in a Russian penal colony.
Issachar's mother, Yaffa Issachar, told NBC News of her anguish at visiting her daughter in prison.
Happening on Twitter
The Pentagon has once again called out North Korean hackers by exposing malware linked to gov-backed hackers, inclu… https://t.co/wWjabRCxN8 shanvav (from Washington, DC) Mon Nov 11 17:23:15 +0000 2019
#CNMF has posted seven new malware samples: https://t.co/cBqSL7DJzI These malware samples are currently used for fu… https://t.co/ZCjMS2A1c1 CNMF_VirusAlert Wed Nov 06 17:27:54 +0000 2019
.@CNMF_VirusAlert posted 7 new malware samples today: https://t.co/X5hXQPQrKU #Cyber #Cybersecurity #InfoSec #CNMF USCERT_gov (from Washington, DC) Wed Nov 06 18:24:32 +0000 2019
Earlier today, #SOUTHCOM's Adm. Craig Faller met w/ leaders & staff at @JDFSoldier's Maritime, Air & Cyber Command… https://t.co/m0eW2Cm0ph Southcom (from Miami, Florida) Thu Nov 07 22:35:25 +0000 2019

No comments:
Post a Comment