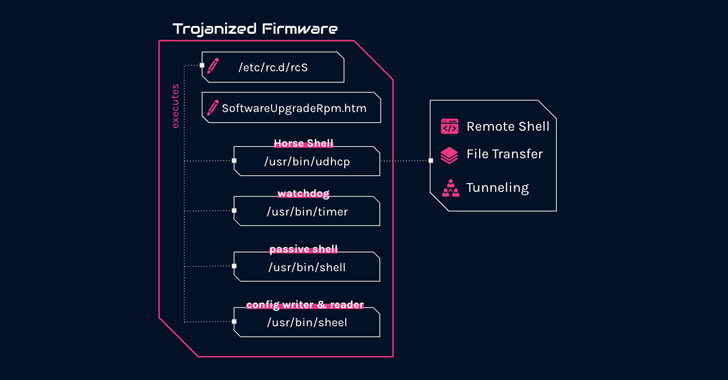
"The implant features several malicious components, including a custom backdoor named 'Horse Shell' that enables the attackers to maintain persistent access, build anonymous infrastructure, and enable lateral movement into compromised networks," the company said .
"Due to its firmware-agnostic design, the implant's components can be integrated into various firmware by different vendors."
Hackers infect TP-Link router firmware to attack EU entities

"It is worth noting that this kind of attack is not aimed specifically at sensitive networks, but rather at regular residential and home networks," explains the Check Point report.
"Therefore, infecting a home router does not necessarily mean that the homeowner was a specific target, but rather that their device was merely a means to an end for the attackers."
Cybercriminals who targeted Ukraine are actually Russian government hackers, researchers say | ...

For years, Russian government hackers have used several made-up personas to hide their tracks and try to trick security researchers and government agencies into pointing the blame in the wrong direction.
The name comes from the group itself, which used illustrations of Fidel Castro and Che Guevara on its dark web site, although no researcher has ever found any evidence that the group has anything to do with the island nation.
What information do hackers need to commit cybercrime?

Currently, more than 90% of American adults use the Internet. The percentage is even higher among younger and middle-aged Americans. Internet users use the global web predominantly for work, study, communication, and entertainment.
All this information helps cyber criminals connect the puzzle pieces and strike. Sometimes data leaks are not the only thing to blame for the lack of privacy – personal information data is often publicly available on public databases for hackers and data brokers to exploit .
This Mustang Mach-E is just "slightly" more advanced than the '74 version my brothers and I drove. Ford is playing… https://t.co/dhDMgZwKKa USAmbChina Wed May 10 02:07:22 +0000 2023
No comments:
Post a Comment