/cloudfront-us-east-2.images.arcpublishing.com/reuters/FZOCLNI7QJPZHKLEYZGZMZMUZ4.jpg)
WASHINGTON, Sept 30 (Reuters) - Suspected Chinese hackers tampered with widely used software distributed by a small Canadian customer service company, another example of a "supply chain compromise" made infamous by the hack on U.S. networking company SolarWinds.
The scope and scale of the hack was not immediately clear. In a message, Comm100 said it had fixed its software earlier Thursday and that more details would soon be forthcoming. The company did not immediately respond to follow-up requests for information.
Mystery hackers are "hyperjacking" targets for insidious spying | Ars Technica

For decades, virtualization software has offered a way to vastly multiply computers' efficiency, hosting entire collections of computers as "virtual machines" on just one physical machine.
Today, Google-owned security firm Mandiant and virtualization firm VMware jointly published warnings that a sophisticated hacker group has been installing backdoors in VMware's virtualization software on multiple targets' networks as part of an apparent espionage campaign.
Hackers leak thousands of Defense Ministry documents
![]()
Carlos Loret de Mola, a Latinus journalist, presented details about the leaked information during his online program on Thursday.
They did not need us to hack to know something that is evident, in Mexico the Government and the Narco are one // No necesitaban que hackearamos para saber algo que es evidente, en México el Gobierno y el Narco son uno
FBI Joins Australian Hunt for Data Hackers

Australia has asked the American FBI to help catch computer hackers responsible for one of Australia's biggest data breaches. Personal details, including home addresses, driver license and passport numbers, of more than 10 million customers of the Singapore-owned telecom giant Optus were stolen.
North Korean Hackers Weaponizing Open-Source Software in Latest Cyber Attacks
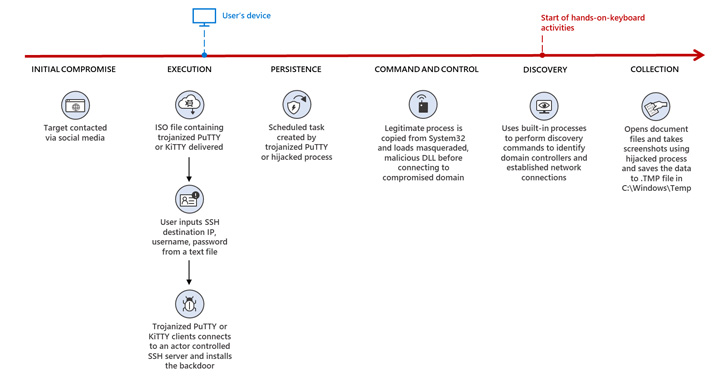
A "highly operational, destructive, and sophisticated nation-state activity group" with ties to North Korea has been weaponizing open source software in their social engineering campaigns aimed at companies around the world since June 2022.
Attacks targeted employees in organizations across multiple industries, including media, defense and aerospace, and IT services in the U.S., the U.K., India, and Russia.
Most hackers need 5 hours or less to break into enterprise environments | CSO Online

Around 40% of ethical hackers recently surveyed by the SANS Institute said they can break into most environments they test, if not all. Nearly 60% said they need five hours or less to break into a corporate environment once they identify a weakness.
The SANS ethical hacking survey , done in partnership with security firm Bishop Fox, is the first of its kind and collected responses from over 300 ethical hackers working in different roles inside organizations, with different levels of experience and specializations in different areas of ...
Hackers Aid Protests Against Iranian Government with Proxies, Leaks and Hacks

The company said it has also witnessed sharing of proxies and open VPN servers to get around censorship and reports on the internet status in the country, with one group helping the anti-government demonstrators access social media sites.
Chief among them is a Telegram channel called Official Atlas Intelligence Group (AIG) that's primarily focused on publishing data associated with government officials as well as maps of prominent locations.
Brazilian Prilex Hackers Resurfaced With Sophisticated Point-of-Sale Malware
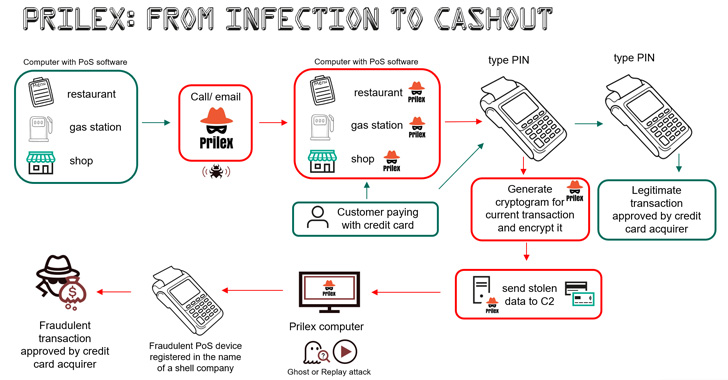
A Brazilian threat actor known as Prilex has resurfaced after a year-long operational hiatus with an advanced and complex malware to steal money by means of fraudulent transactions.
"The Prilex group has shown a high level of knowledge about credit and debit card transactions, and how software used for payment processing works," Kaspersky researchers said .
How hobbyist hackers are preserving Pokémon's past—and shaping its future | Ars Technica

Earlier this year, Pokémon Legends: Arceus reinvigorated developer Game Freak's iconic series by shaking up a formula that had gone largely unchanged for more than 25 years. But that recent bout of experimentation doesn't diminish just how long the Poké-formula has remained mostly static.
CISA: Hackers exploit critical Bitbucket Server flaw in attacks

The Cybersecurity and Infrastructure Security Agency (CISA) has added three more security flaws to its list of bugs exploited in attacks, including a Bitbucket Server RCE and two Microsoft Exchange zero-days.
CISA's Known Exploited Vulnerabilities (KEV) catalog now includes two Microsoft Exchange zero-days (CVE-2022-41040 and CVE-2022-41082) exploited in limited, targeted attacks, according to Microsoft.
Exclusive: Suspected Chinese hackers tampered with widely used software distributed by a small Canadian customer se… https://t.co/b3s0w0b1Kp Reuters (from Around the world) Fri Sep 30 15:14:15 +0000 2022
Suspected Chinese hackers tampered with widely used Canadian chat program -researchers https://t.co/K1KmsJ9UBV https://t.co/SoUwxdV8OR Reuters (from Around the world) Fri Sep 30 21:25:33 +0000 2022
Army of the Alien Monkeys
Earth is nice. We want it.
We welcome your submission to us.
No comments:
Post a Comment