
Hackers can covertly turn a cable inside a computer into a makeshift antenna that can secretly transmit sensitive data, even from “air-gapped” devices that are deliberately not connected to the internet.
Air-gapped computers are commonly used by government security services and key infrastructure control systems to prevent remote hackers from gaining access, but that doesn’t mean it is impossible to get data out.
Hackers Increasingly Using WebAssembly Coded Cryptominers to Evade Detection

Web security company Sucuri, which published details of the campaign, said it launched an investigation after one of its clients had their computer slowed down significantly every time upon navigating to their own WordPress portal.
"Once decoded, the contents of auto.js immediately reveal the functionality of a cryptominer which starts mining when a visitor lands on the compromised site," Sucuri malware researcher Cesar Anjos said .
Hackers Exploit PrestaShop Zero-Day to Steal Payment Data from Online Stores

Malicious actors are exploiting a previously unknown security flaw in the open source PrestaShop e-commerce platform to inject malicious skimmer code designed to swipe sensitive information.
"Attackers have found a way to use a security vulnerability to carry out arbitrary code execution in servers running PrestaShop websites," the company noted in an advisory published on July 22.
Hackers scan for vulnerabilities within 15 minutes of disclosure

System administrators have even less time to patch disclosed security vulnerabilities than previously thought, as a new report shows threat actors scanning for vulnerable endpoints within 15 minutes of a new CVE being publicly disclosed.
According to Palo Alto's 2022 Unit 42 Incident Response Report , hackers are constantly monitoring software vendor bulletin boards for new vulnerability announcements they can leverage for initial access to a corporate network or to perform remote code execution.
Hackers steal $6 million from blockchain music platform Audius

The decentralized music platform Audius was hacked over the weekend, with threat actors stealing over 18 million AUDIO tokens worth approximately $6 million.
Audius is a decentralized streaming platform hosted on the Ethereum blockchain where artists can earn AUDIO tokens by sharing their music, and users can earn tokens by curating and listening to content.
U.S. doubles reward for tips on North Korean-backed hackers
The U.S. State Department has increased rewards paid to anyone providing information on any North Korean-sponsored threat groups' members to $10 million.
These increased bounties add to rewards of up to $5 million announced by the State Department in March for info on DPRK-backed threat actors targeting crypto exchanges and financial institutions worldwide to support the North Korean regime's illicit activities.
Critical FileWave MDM Flaws Open Organization-Managed Devices to Remote Hackers

FileWave's mobile device management (MDM) system has been found vulnerable to two critical security flaws that could be leveraged to carry out remote attacks and seize control of a fleet of devices connected to it.
"The vulnerabilities are remotely exploitable and enable an attacker to bypass authentication mechanisms and gain full control over the MDM platform and its managed devices," Claroty security researcher Noam Moshe said in a Monday report.
Experts Uncover New 'CosmicStrand' UEFI Firmware Rootkit Used by Chinese Hackers
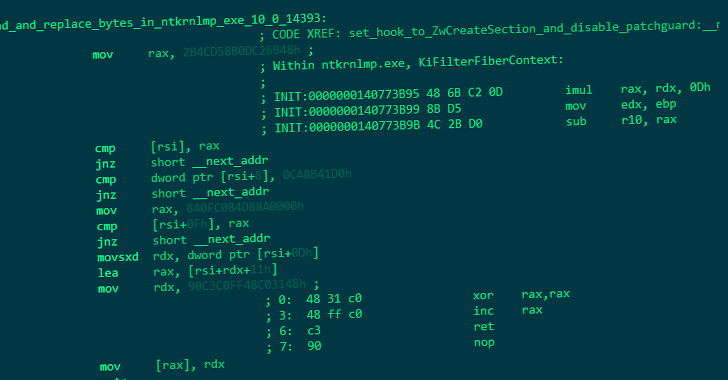
An unknown Chinese-speaking threat actor has been attributed to a new kind of sophisticated Unified Extensible Firmware Interface ( UEFI ) firmware rootkit called CosmicStrand .
"The rootkit is located in the firmware images of Gigabyte or ASUS motherboards, and we noticed that all these images are related to designs using the H81 chipset," Kaspersky researchers said in a new report published today.
System Unknown NFT Collection
#NFT #ETH #nftgiveaways #nftcommunity #Giveaways #NFTPromotion #ART
https://opensea.io/collection/systemunknown
Check out the System Unknown artwork. Click here.
No comments:
Post a Comment